A Lesser Known Resource That Can Help You Spot a Phish ![]()
Table of Contents
Phishing vs. Spear Phishing
Phishing emails are one of the most common attack tools used by cybercriminals. According to the ZDNet, over 3 billion phishing emails are sent every day, which accounts for 1% of all email traffic.
Phishing emails are cleverly disguised to look like they came from a person or company you know or trust, and can be used to deliver malware via an infected attachment or direct the recipient to a lookalike website designed to steal user credentials from their target.
Spear phishing emails are a type of phishing email that is well-researched and highly personalized. Spear phishing campaigns are highly targeted to a specific person or organization, and they often include relevant details that make the email more compelling.
The goal of spear phishing is to compromise a high-value target, such as a CEO, with a message that is more believable to the intended victim than other forms of phishing that apply a more broad strokes approach.
If you’re a business owner, manager, or possess a unique level of access within your company, such as an administrative assistant or superuser, you’re a prime target for spear phishing. Cybercriminals know that by hacking into the email accounts of people who hold positions of authority, they will be more likely to obtain valuable data or commit financial crimes.
How to Spot a Phishing Email
There is some good news. Most phishing emails never actually reach their intended recipients. The vast majority of phishing attempts are thwarted by email spam filters and other security tools. Google says they block 100 million harmful emails from reaching Gmail users each day.
This means that the small percentage of phishing emails that we receive in our inboxes make it past the first round of checks.
When you suspect an email you’ve received may be a phishing attempt, it’s a good idea to carefully review the email contents before clicking any links, opening any attachments, or downloading and viewing any images.
The most convincing phishing emails usually have these common characteristics
1 – The email seems plausible. If the email looks phony, then no one will click on it. While some people are more gullible than others, most of us know not to believe emails claiming to be sent from Nigerian Princes or anyone else who wants to give us free money.
2 – The email has the right tone and pretext. Little stylistic details matter. If an email is coming from Microsoft or Apple, we would expect that the logo, color, fonts, and style match that company’s official brand. The writing style would be expected to sound professional and cordial, not bullying or aggressive. Context is also important. Their reason for contacting you has to make sense.
3 – The sender is someone you know or trust. This is where things get tricky. Just because the sender’s information appears to match the name and/or email address of someone you know, it doesn’t mean they were the true sender of the email. This is where spoofed, or falsified, email headers come in.
What’s an Email Header
Every email is comprised of three key components: the envelope, the header, and the message.
You won’t ever see the envelope because it’s mainly used for internal processing between email systems. The message body is the part that we always see because it is the actual contents of the message sent. The email header is visible to email senders and recipients, but you have to know where to find it.
The header contains identifying information about the email, such as the sender, recipient, date, and subject. It also contains a wealth of interesting data about the route the email took to get to its recipient, and whether it passed a series of authentication checks along the way.
While email headers can be manipulated like other aspects of the email, doing so requires some level of sophistication. This is why email headers can be a helpful resource to identify potential phishing emails. Any information that doesn’t match, or is unusual in any way, may indicate a potential phish.
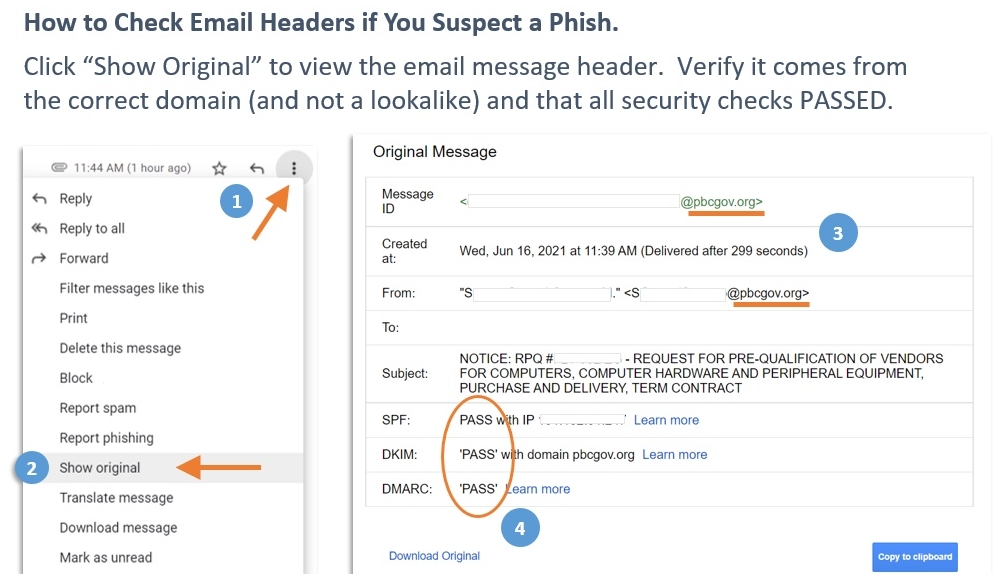
Last week, I got an email that I suspected might be spear phishing.
The domain was from “pbcgov.org” and that combination just didn’t seem right. Even though I have good email security, I know no tool can catch 100% of fakes. So I checked the email headers (and did my own independent research) before I clicked on the link.
And I’m glad that I did because the email was legitimate.
3 ways email headers can help you spot a phish
Verification checks fail
Without getting into the nitty-gritty technical details, there are 3 types of verification checks a properly configured set of emails should PASS: DKIM, SPF, and DMARC.
In the header, you can easily see PASS/FAIL for each. A check that fails might just be a misconfiguration, but it also could be an indication of a spoof.
Mismatched sender addresses or domains
Not every inconsistency is an indicator of a phish, however, the values should not be vastly different.
For example, this might make sense:
“smtp.mailfrom” value – suzy@company.com
“From:” value (seen by recipient) – offers@company.com
Whereas this might not:
“smtp.mailfrom” value – hacker@scam-you.com
“From:” value (seen by recipient) – offers@company.com
Email travel path and email client
Most emails originate from a client (i.e. Outlook, Gmail), and all emails pass through at least 2 servers (source, destination), but often more. These are interim hops are visible in the header.
For an email supposedly sent from the US, it would be suspicious if the originating server was in another country or sent from an unusual mail client.
There are many ways to spot a phishing email. The best and easiest is with enterprise-grade email security software, or through the features of a robust anti-malware program.
However, since no tool is without flaws, it’s good to know what else to look for.