If you forget to take appropriate precautions, ransomware can hold your device hostage and encrypt your personal files. Learn how to minimize this risk and what to do if your company becomes its victim.
Table of Contents
What is ransomware?
The term ransomware was created from a combination of words ransom and software. It is used to describe a type of malicious software that makes the use of devices such as computers, laptops, tablets and smartphones nearly impossible – by blocking the screen, encrypting files or even preventing the operating system from starting.
After a machine has been compromised by ransomware, hackers display a message on the screen and demand the user pay a ransom–usually in the form of a hard to trace cryptocurrency like Bitcoin–for unlocking access to the device. Most instances of ransomware are perpetrated by cybercriminals seeking financial gain.
How does it work?
There are hundreds of variants of ransomware, but what is important to know, is that they all function the same way – they all combine blackmail and data encryption.
- The relatively simplest group of ransomware to remove is screen-lockers, i.e. programs that block the screen of your phone, computer or any other device.
- Ransomware that encrypts private files on your device (e.g. Cryptolocker) can be much harder to overcome without paying a ransom.
- So-called disk-encryptors can encrypt your entire device, preventing the operating system to start.
How does it spread?
Ransomware infects a system most often through downloaded and opened device files or Internet services that exploit the weaknesses of the browser. In the first case, most often malicious files are delivered as attachments to unsolicited emails (spam) and are often disguised as important documents such as invoices or order confirmations, or other tempting data, such as “private pictures” or interesting videos. . Ransomware can also be attached to pirated content downloaded from the web. In the second case, ransomware impersonates sub-ads on popular websites and exploits vulnerabilities in the operation of web browsers and their plug-ins.
What can you do to reduce the risk of infection?
Maintain encrypted Backups
It’s not easy to secure your files from all types of attacks when ransomware developers are constantly innovating them. The only foolproof defense is to mitigate the possible effects of the attack. Each user in the network and the server should be protected with a series of backups that can be easily restored and are stored offsite, ideally air-gapped from your main computer network so they cannot also be infected. The simplest way to do this is with a modern cloud backup solution.
Perform regular software and operating system updates
Every computer with Internet access should use anti-virus, anti-spyware and firewall programs which protect the device from external attacks coming from the web. It is particularly important to keep these up-to-date and to scan your devices regularly. Also, never postpone critical operating system updates or security patches for more than 24 hours.
Ensure your servers have proper security controls
It is also important to remember to schedule regular vulnerability tests. With them you’ll easily discover the security gaps in your company’s infrastructure. The scope of such weaknesses can be wide, from errors at the system configuration level, through the use of outdated versions, to software defects. Basic vulnerability tests are performed using a vulnerability scanner, i.e. a program that contains a set of known errors and gaps.
Take extra care when opening e-mails
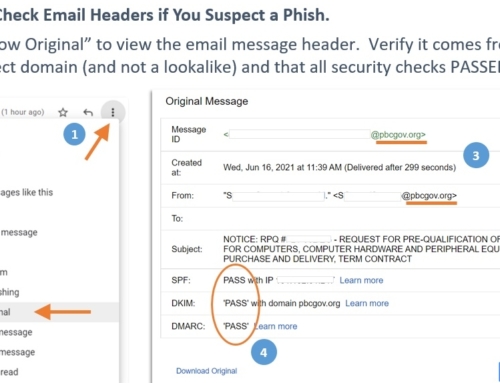
Never open an attachment or click links that you don’t trust. Sometimes the threat takes the form of an empty .pdf file with a hidden network link to a dangerous program that will be installed on your device. Pay close attention to the sender’s email address, not just their display name, as well as the recipient field and the URL of any embedded links. You can check a URL target by hovering over a link before clicking on it. Be sure any links go directly to trusted websites you know, or better yet, skip the link altogether and visit the site directly by typing it into your browser.
Don’t underestimate the human element
Ensure all staff attends regular security awareness training. You can engage a knowledgeable IT security firm for this, and also ask them to perform regular IT health checks reviews or security audits on your behalf. Lastly, use common sense and limit the number of administrative accounts in your company to the minimal necessary.
What should you do if an attack occurs?
Unplug affected computers from the network
If you suspect that your computer might have been attacked by ransomware, the first step is to take it offline. This means: physically disconnecting the Ethernet cable, turning off the Wi-Fi network, and switching off the machine. Several types of ransomware can spread over a network connection, so the faster you disconnect potentially infected computers from the network, the greater the chance that other devices will be saved.
Disable shared network drives
More and more ransomware variants, such as CryptoFortress and Locky, will be able to encrypt shared network drives connected to the infected computer via the local network. If you find that you have infected even one computer that is connected to the corporate network, then it is a good idea to physically disable network drives while you work on cleaning the malicious software off the network.
Question the victim
After turning off the computer and cutting off network drives, the next step is to talk to the user whose machine has been infected. What were they doing before the ransomware infection? Did they receive any strange, unusual emails? Did they click any uncommon links, and if so, which and where. It is necessary to devote time to make your employees aware of the threats lurking in the network. Such training will help protect the company network from the next attack.
Notify other users of the threat
Once you know what kind of infection you are dealing with, you should notify other network users about the possibility of infection so they can make backups of their systems and be alert to the potential of any subsequent attacks.
Run security scans
Now that any machines with confirmed or suspected malware have been turned off and the rest of the users have been warned, check the software updates on all computers and run a scan of all devices on the network. Ransomware moves and evolves quickly, so it’s important to have the latest versions of anti-virus and anti-malware software installed on all computers across your entire network.
What should you do with an encrypted computer?
You will most likely need to wipe the entire contents of the disk and install the whole system from scratch, starting with a fresh operating system installation.
If you have up-to-date backups, you can restore the entire system, or select files from that backup. However, before doing so, you need to be confident your backup is “clean” and was taken before the infection started. Be aware that ransomware can be present on a system, but in a dormant state for hours or days before being detected by the user.
You should try to find out the name of the ransomware variant you’ve been attacked with. Also consider contacting a specialized IT security firm and/or local law enforcement to report the incident and obtain decryption tools and other resources to help you remediate the infection without paying the ransom. The FBI works closely with local law enforcement agencies and cyber security experts to share information about attacks and how to stop cybercrime.
If you must, you can pay the ransom to regain access to your systems. But remember, paying a ransom should be the last resort. Experts advise against this approach – paying a ransom only encourages cybercriminals by rewarding them for these attacks. If you do decide to pay, first make sure that the blackmailers can and will unlock your files by decrypting a sample beforehand, and then negotiate the price.
How can you prevent future attacks?
If ransomware got into your network, it means that one, or likely several security controls were missing or inadequate, and you need to find and fix the holes as quickly as possible. The best way to find them is to hire a reputable IT security company that will conduct a comprehensive vulnerability scan of your business. It’ll allow you to identify the security gaps and take recommended actions so as to remediate the problem before it occurs – that is before your company becomes the victim of cybercrime.
If you would like a complimentary consultation with eSilo experts to discuss how we can help you prevent unexpected downtime from a ransomware attack or other computing disaster, or if you’re interested in a full IT audit of your systems and network security, contact us online or by phone 561-747-6880.